How Can You Spot and Avoid a Modern Scam Email?
Scam emails have become nearly indistinguishable from legitimate messages. Learn how phishing tactics evolved and how to spot red flags before it’s too late.

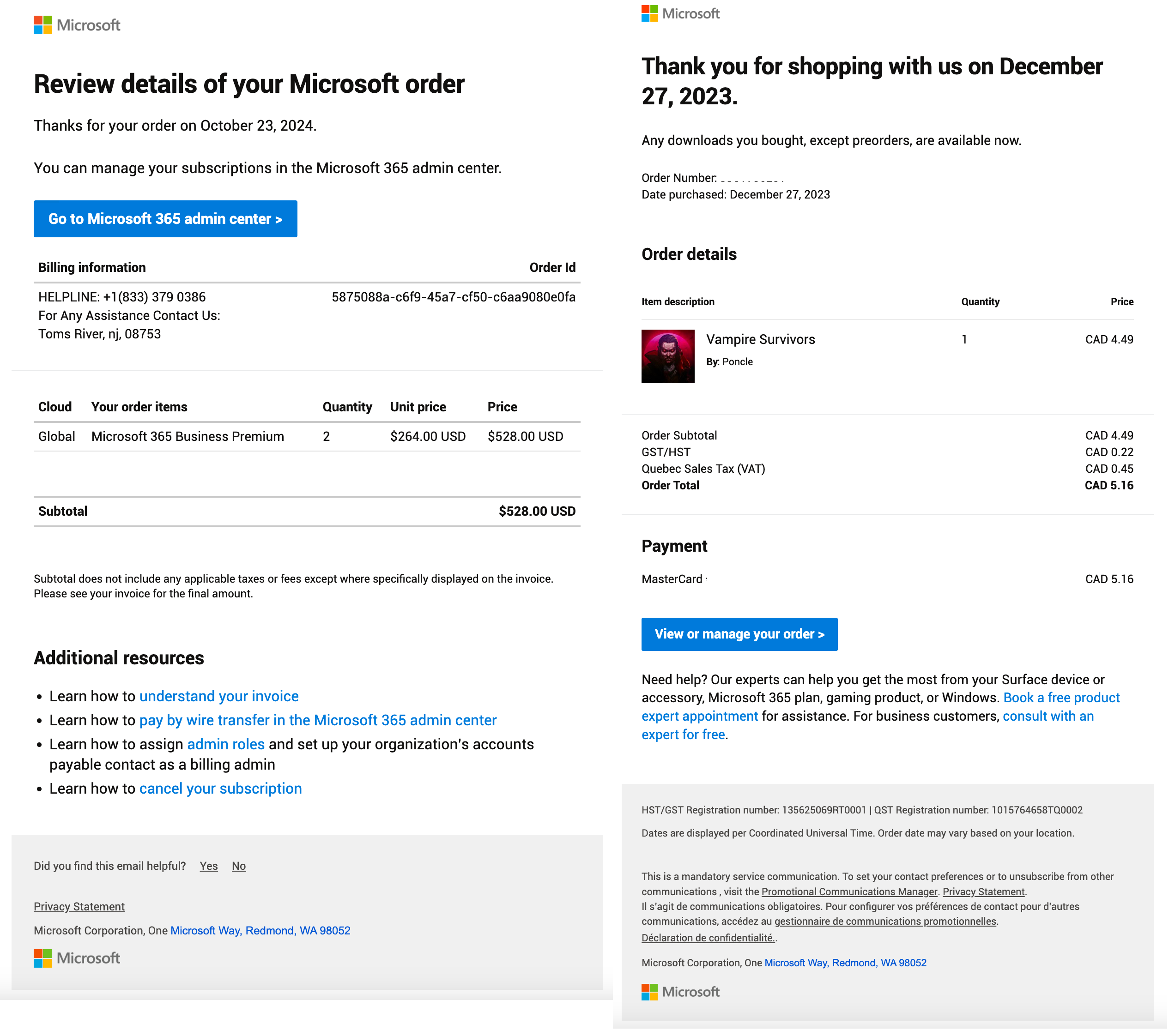
It started with what looked like a routine invoice. The message claimed that two Microsoft 365 Business Premium licenses had been purchased for a total of $528. The formatting was polished. The logo matched Microsoft branding. Even the links pointed to real Microsoft domains. But one detail didn’t quite fit: the support phone number.
A quick search revealed that the number belonged to a known scam operation. The invoice was fake: an elaborate phishing attempt designed to create panic and trigger a phone call. These scams are not new, but they’ve evolved dramatically in sophistication. And they now blur the line between email deception and voice fraud. This article explores how phishing emails work, how phone scams are intertwined, and what signs to watch for to protect yourself and others.
What Is a Phishing Scam?
Phishing scams aim to extract money or personal information by impersonating trusted entities. Most rely on creating a false sense of urgency: a surprise charge, a security warning, or a message claiming legal consequences. The goal is to make the recipient act quickly—usually by clicking a link or calling a fraudulent support number.
While anyone can be targeted, these scams often succeed against less tech-savvy individuals. However, with professional formatting and stolen branding, even experienced users can be caught off guard. Phishing emails typically fall into three major categories:
- Information Theft: These emails ask recipients to enter sensitive data—such as passwords or credit card numbers—into a fake form or website.
- Phone Scams (Vishing): These emails direct recipients to call a fake support number, where scammers escalate the deception and pressure victims into sending money, often through gift cards or wire transfers.
- Malware Installation: These messages trick users into downloading malicious software that steals information, encrypts files for ransom, or silently opens backdoors for future attacks.
Many phishing emails combine multiple tactics to maximize the likelihood of success.
A Look at a Modern Phishing Example
The scam invoice received by Technodabbler was strikingly realistic. The subject line referenced a legitimate product. The layout matched Microsoft branding. Some of the links even pointed to real Microsoft domains, likely used to establish trust.
However, a few subtle inconsistencies revealed the truth:
- Suspicious Contact Details: The listed phone number, +1 (833) 379 0386, was not a verified Microsoft support number. A quick search linked it to other reported scams.
- Unfamiliar Locations: The invoice referenced a support center in Toms River, New Jersey—a far cry from Microsoft’s headquarters in Redmond, Washington.
- Generic Language: The email used vague salutations like “Dear Customer.” Legitimate communications from companies usually include your name or account information.
- Masked Links: Some buttons appeared legitimate, but the actual URLs (visible by hovering) did not match official Microsoft domains.
These tactics work because they exploit common behaviors. People are more likely to trust polished emails, especially when they’re tired or in a hurry. Scammers intentionally time their attacks for early mornings, late evenings, or weekends.
Spotting and Avoiding Scams
As phishing tactics evolve, the best defense is a skeptical mindset. Here are some guidelines to help identify potential scams:
- Always hover before you click: Verify that links point to legitimate domains. A button might say “microsoft.com,” but the link may actually lead elsewhere.
- Manually visit company websites: Never use contact info from an unsolicited email. Instead, type the company's URL into your browser and find the contact page. If you don't know the URL, use a trusted search engine.
- Watch for urgency: If an email tells you to act immediately or face consequences, that’s a red flag. Scammers rely on fear to short-circuit decision-making.
- Beware of odd formatting or language: While modern phishing emails are well-designed, many still include subtle grammar errors, off-brand fonts, or awkward phrasing.
- Check the domain name closely: Some scammers use lookalike domains like
micr0s0ft.com, replacing letters with numbers or adding extra words to confuse users. Depending on the font, lookalike domains like micr0s0ft.com can be difficult to spot.
Above all, trust your instincts. If something feels off—even slightly—it’s worth pausing to investigate.
Fighting Back: Awareness Is Key
Despite law enforcement efforts and growing public education, scam centers continue to thrive. When one gets shut down, another takes its place. Their success depends on volume and victims who don’t know better.
That’s why spreading awareness is crucial. Talk to family members, especially those less familiar with digital risks, about common phishing techniques. Share examples. Point them to resources. The more people understand the signs, the fewer successful scams will occur.

Phishing has evolved from sloppy misspellings and obvious forgeries to professional-looking communications that fool even seasoned users. But the underlying tactics remain the same: instill fear, impersonate authority, and rush the victim.
By taking a moment to verify, reflect, and investigate, you can protect yourself—and others—from becoming the next target.






